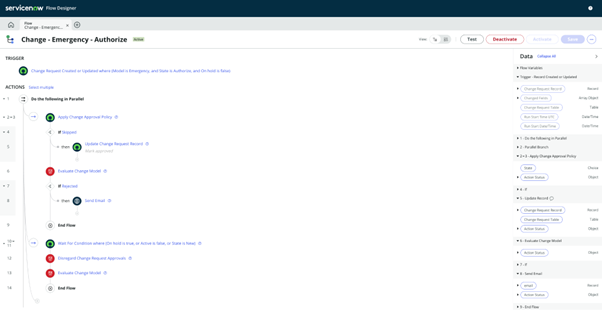
Flow Designer:
The theming changes were made to Flow Designer. App Engine and Flow Designer lagged from a colour scheme perspective, still showcasing our old pastel branding. They have now been replaced with our new, more neon-looking palette.
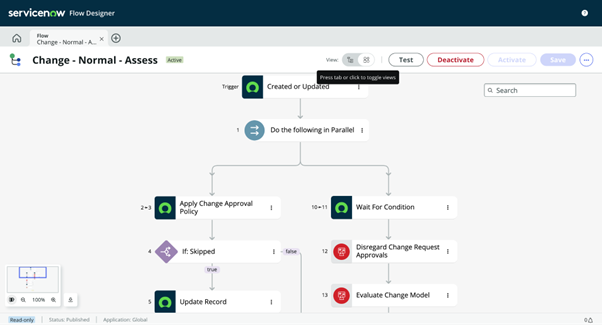
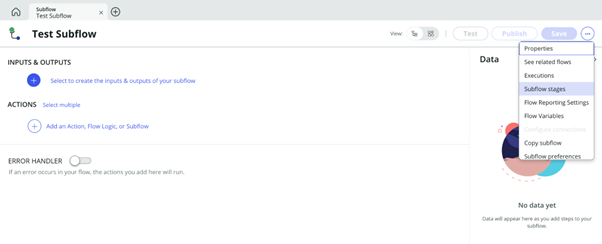
In Subflow functionality, the purview has expanded within Flow Designer. Subflows can now be used in the Diagramming view and have stages enabled within them.
Previously, some API calls were happening behind the scenes that were making certain aspects of Flow Designer run slower than optimal. Some of these were removed entirely and others went through an optimization overhaul to improve their performance.
- 60% Flow load time reduction
- 98% Time reduction for adding Subflows to a parent flow.
- 99% Flow logic optimization time reduction
The new homepage revamp debuted in Vancouver, it was a standard List view of all of your Flows, Subflows, Actions, etc. This has been replaced with a much more dashboard-like experience. The lists still remain; however, you can filter them all down to the work you have created with the click of a toggle. In the upper right-hand corner, you will be able to easily pick up on what they were most recently working on by showing the last 3 artefacts you opened. You can see what progress your team has been making below that and track the execution status through reports.
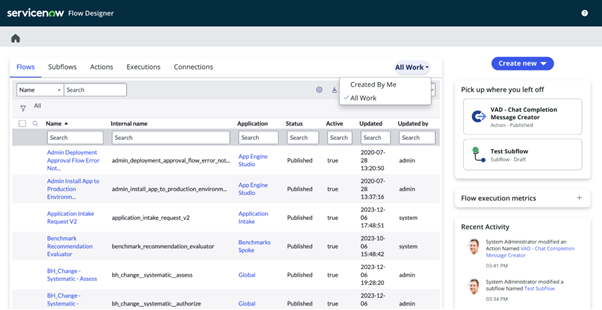
Data Pills are those little bubbles you see within the Flow Designer interface, representative of the values or Objects the actions and logic are running off of. Previously, when a developer had created a data pill, there was no way to edit it. In Vancouver, in both the standard and Diagramming view, you will now be able to double-click into a pill to edit it, saving time and reducing the chances of mistakes being made.
Using the GenerativeAI large language model, as you build your Flows, ServiceNow will make guesses as to what action or logic route should be used next.
In Vancouver, the recommendations are being made off an internal ServiceNow model, based on the Flows and automation that runs all our cloud solutions and using best practices.
Application Manager:
It provides admins the ability to install, update, and manage licensed applications and plugins for their instance. Application Manager features a new UI experience with support that improves the ability to locate applications and plugins.
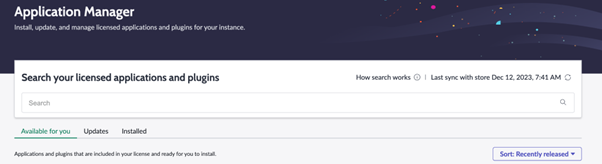
The Available for You page displays applications and plugins that are included in your license and ready for you to install. An auto sync with the store happens every 24 hours, if an entitled app isn’t displaying in Application Manager, you can manually sync using the sync button.
The Updates page displays applications and plugins that are ready for you to update. If there are updates available, they’re displayed, and a green Update available message is displayed on the tile.
The Installed page displays applications and plugins that are currently installed on your instance. Installed applications and plugins display their current version, as well as notifying you that your version is up to date.
Service Catalog :
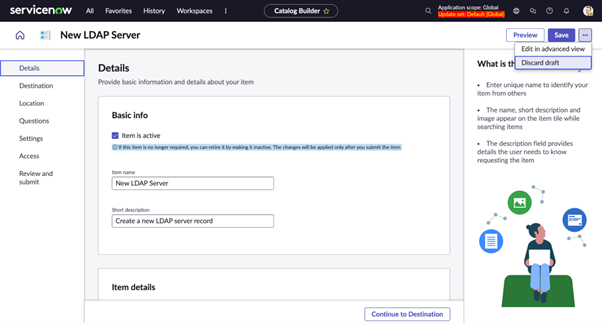
The Service Catalog application provides a requester view of the available services and products offered by the departments within your organization. Catalog Builder users can discard draft items seamlessly, improving workflow and audit history.
- Discard the catalog items that are in the Draft state directly in the Catalog Builder by using the Discard Draft button displayed for the catalog item.
If you no longer want a draft item, you can discard it in Catalog Builder. When you discard a draft item that doesn’t have a published item associated with it, that draft item is deleted. If a draft item has a published item associated with it, the draft item is deleted while the published item remains intact. The data of the catalog item is reverted to the state that it was in before you started editing it.
Procedure
- Navigate to All > Service Catalog > Catalog Builder.
- Select the Catalog items tab.
- Select the catalog item that you want to discard. Note: You can discard only those catalog items that are in the Draft state. After you select any draft item, the Discard draft button becomes active.
- Select Discard draft.
Change Management - Data Archiving:
You can activate the Change Management - Data Archiving plugin (com.glide.auxdb) if you have the admin role. The Change Management - Data Archiving plugin (com.glide.auxdb) enables to move of a subset of data from large tables into the data archive.
Archive the change requests, change tasks, and conflict data in your instance per your data retention policy through the updated archive rule, which enables you to include the conflict table with change requests and change tasks.
Access Analyzer:
ServiceNow Access Analyzer is an application that helps the administrators and developers to view permissions for the selected user, role, or group. It enables you to analyze and view the permissions of the user, group, role for a table, Client callable script include, UI page, and REST endpoint.
Access Analyzer impersonates the identity record to retrieve details about the permissions and doesn’t read or store any personal or sensitive data of the identity. Access Analyzer has limitations in accurately evaluating access of the resources related to managed scope resources and delegated developer.
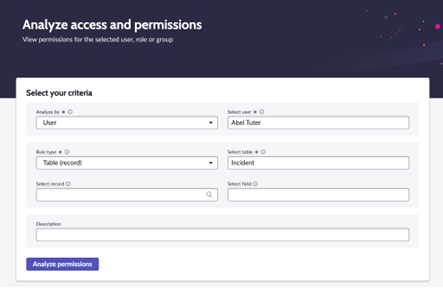
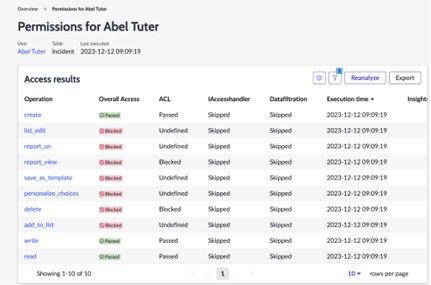
The following are some of the benefits of using the Access Analyzer:
- Analyze access to resources (tables).
- Generate a report on if an identity has access to a resource (table).
- Understand who has access for a critical security hygiene.
- Prevent from over-provisioning permissions.
- Achieve the least privilege principals when implementing access controls.
- Limit access to certain data, which includes applications, tables, rows or columns, and other resources.
- Provides reporting capabilities for the analyzer results.
ServiceNow Zero Trust Access:
ServiceNow Zero Trust Access product spotlights ServiceNow's commitment to providing a highly secure strategic platform to build business workflows and simplify processes. Cybersecurity strategy and data breach prevention are frequent topics at company boardroom meetings. The Zero Trust Security Architecture framework provides guidelines for businesses to operate efficiently with reduced risk and minimal friction. ZTA aims to help customers achieve a better overall security posture and improve user security.
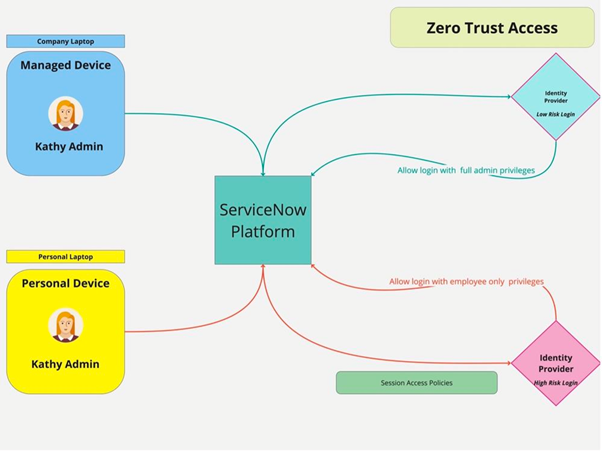
The Zero Trust Access security architecture assumes no user or device is trusted by default. This means that all access to applications and data is granted on a least privilege basis only after the user's identity has been verified and the risk of the request has been assessed.
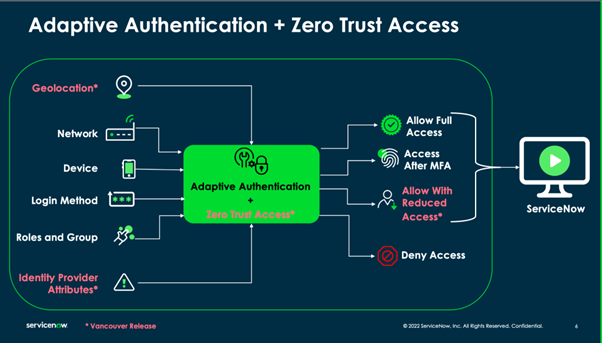
It enables the security admins to reduce or limit user access in a session based on IP, Location, Identity provider attributes, and user attributes using adaptive authentication policies.
- Session Access configurations can only be performed with security_admin role. You must elevate your role to security_admin.
- Session Access is a web only feature and doesn’t support mobile app logins.
- Session Access doesn’t support integrations.
- Session Access has no impact, if the reduced or limited role isn’t assigned to a user, then there are no changes to the logged in session. The user continues to access the instance with the assigned privileges.
- Session Access has no impact, while the user is already logged in to the instance and simultaneously the admin configures the policy. The user has to log out from the session for the policy to be effective.
- Session Access has no impact, when the user is in a trusted network, later switched to VPN (change in location or network) within a session.
- Session Access is enforced at the time of login. Any change in risk parameters during the session won’t result in reduced access. For example, A user switching from corporate network to untrusted network after establishing the session, won’t result in reduced access. Unless the user logs out and logs in again.
Dynamic privilege reduction is implemented using adaptive authentication policies. These policies use attributes like device status(managed/unmanaged), risk score, etc., shared by the organization's SAML-based identity provider along with IP address, location, and authentication method used for login for assessing risk. After verifying the user's identity, ZTA policies will be evaluated to assess the risk of the request. Based on the results of this assessment, ZTA will then dynamically reduce the user's privilege in the session to the appropriate level configured by the security administrator.
-1-1.png?width=1500&height=583&name=Poorna_2_Logo_Vector_Kaptius_Final_file-03%20(1)-1-1.png)

-1.png)